Erik Hjelmvik
,
Saturday, 12 February 2011 15:01:00 (UTC/GMT)
Switching protocol from unencrypted HTTP to encrypted HTTPS is a good move in order to help the users of a website to protect their privacy online.
Many webmail providers have therefore started rolling out their encrypted services during the past few years.
Google announced their optional “always use https”
setting back in 2008 and also provided some guidance as to why it was important to use HTTPS:
Https keeps your mail encrypted as it travels between your web browser and our servers,
so someone sharing your favorite coffee shop's public wifi can't read it.
It took Microsoft Hotmail until November 2010 to announce their optional support for HTTPS encryption,
which users could activate by visiting https://account.live.com/ManageSSL.
Adding the option to manually turn on encryption seems to satisfy most people in the security community,
probably since it enables us geeks to protect our privacy online through encryption.
But the majority of the webmail users online are not aware of the risk of getting their traffic sniffed
and do also not know how to turn the encryption feature on.
The encryption must therefore be turned on by default in order to protect the broad mass of webmail users.
An open letter written by some well known security profiles,
such as Jacob Appelbaum, Richard Clayton,
Roger Dingledine, RSnake, Jeff Moss, Ronald L. Rivest and Bruce Schneier,
was sent to Google in June 2009.
In the letter the authors requested that Google should turn on encryption as part of the default settings:
Rather than forcing users of Gmail, Docs and Calendar to “opt-in” to adequate security, Google should make security and privacy the default.
The letter also mentioned that other competing webmail providers had even worse security since they didn't even provide any “opt-in” encryption at that time:
Google is not the only Web 2.0 firm which leaves its customers vulnerable to data theft and account hijacking.
Users of Microsoft Hotmail, Yahoo Mail, Facebook and MySpace are also vulnerable to these attacks. Worst of all – these firms do not offer their customers any form of protection.
But how many of the major webmail providers do actually provide HTTPS as the default protocol today?
We will in this blog post look closer at two major webmail services online: Gmail and Hotmail.
GMAIL
Just like most other webmail services Google's Gmail use HTTPS to encrypt the username and password while logging in.
But Gmail now also provide encryption by default also after the user has logged in.
This prevents hackers as well as investigators/analysts from extracting sent emails by sniffing network traffic.
Hackers have on the other hand been able to take over other users' logged in Gmail sessions for some time by sniffing the GX cookie
and using it to fool Gmail that they are logged into the victim's user account.
Google have now mitigated this issue by adding encryption and setting the GX cookie to “Secure connections only”,
which means it will only be sent in HTTPS sessions.
There is, however, another cookie parameter used by Gmail that is allowed to be sent across an unencrypted HTTP session.
This cookie is called “gmailchat” and is typically submitted when visiting http://mail.google.com/mail.
This cookie parameter is picked up by NetworkMiner and displayed on both the Credentials tab as well as the Parameters tab.
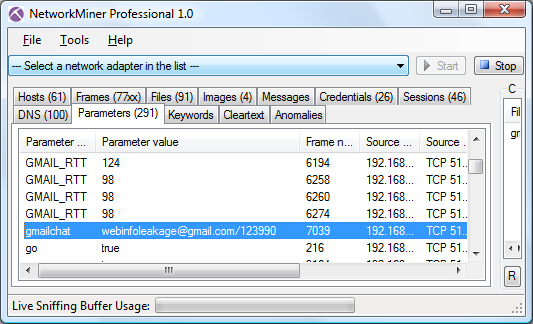
The client IP address, login time and Gmail account of a gmailchat cookie
can be used as evidence by an analyst in order to determine which person that was using a particular computer at a particular time.
HOTMAIL
The security in Hotmail is much worse than that of Gmail.
With default settings only the login is protected with encryption, everything after that is sent in cleartext HTTP.
This makes it possible to extract emails sent with Hotmail just by passively sniffing the network traffic from a logged in Hotmail user.
In our recent “TCP/IP Weapons School” blog post
we showed how NetworkMiner displays extracted emails in the Messages tab, this feature works just as well also with Hotmail traffic.
By loading a pcap with Hotmail web traffic into NetworkMiner you would get something like this:
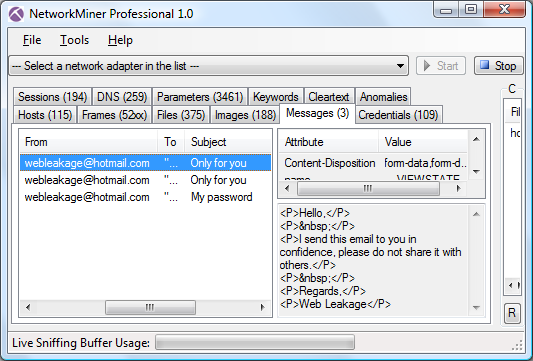
You can also use the Parameters tab to look for parameter names “fFrom”, “fTo”, “fSubject” and “fMessageBody”
and thereby manually extract who sent and received the email as well as read the subject and message of the email.
These parameters are all sent in an unencrypted HTTP POST to mail.live.com.
So if you're using Hotmail or Windows Live Mail, make sure to visit https://account.live.com/ManageSSL and enable the encryption functionality!
Posted by Erik Hjelmvik on Saturday, 12 February 2011 15:01:00 (UTC/GMT)
Tags: #Hotmail
#SSL
#HTTPS
#NetworkMiner