Chinese MITM Attack on iCloud
Users in China are reporting a MITM attacks on SSL connections to iCloud.
GreatFire.org, who monitor the Great Firewall of China (GFW), also published a
blog post on their website earlier today saying:
This is clearly a malicious attack on Apple in an effort to gain access to usernames and passwords and consequently all data stored on iCloud such as iMessages, photos, contacts, etc.
Fake SSL Certificate
In their blog post GreatFire also linked a packet capture file, which we have analyzed in order to verify the MITM attack. We loaded the PcapNG file into NetworkMiner Professional and extracted the X.509 SSL certificate.
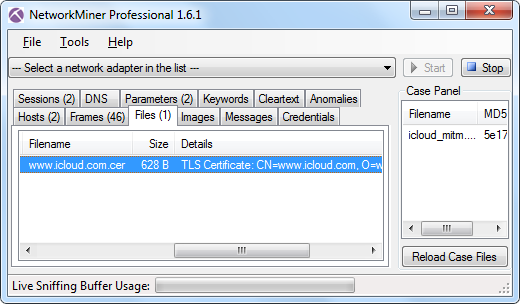
The extracted certificate can be downloaded from here. Also, here are a few details from this X.509 certificate:
$ openssl x509 -inform DER -in www.icloud.com.cer -noout -issuer -subject -startdate -enddate -fingerprint
issuer= /C=cn/O=www.icloud.com/CN=www.icloud.com
subject= /C=cn/O=www.icloud.com/CN=www.icloud.com
notBefore=Oct 4 10:35:47 2014 GMT
notAfter=Oct 4 10:35:47 2015 GMT
SHA1 Fingerprint=F4:68:B5:F3:FE:D8:07:97:44:76:A2:2B:32:EA:31:37:D9:24:F7:BA
As reported elsewhere, the certificate was self signed, which means that browsers and most iPhone apps will either inform the user about the connection being unsafe or simply close the connection (see update at the bottom of this blog post regarding the missing certificate verification in Apple iOS). This use of self signed certificates is consistent with previous SSL MITM attacks performed in China against GitHub, Google, Yahoo and live.com.
Location of the MITM Attack
By looking at host the information provided by NetworkMiner for the fake iCloud SSL server we can see that it is just six router hops away from the client (having an IP TTL value of 58). This indicates that the MITM attack is being performed within China, since we'd expect to see at least three more router hops if the packets were coming from outside China.
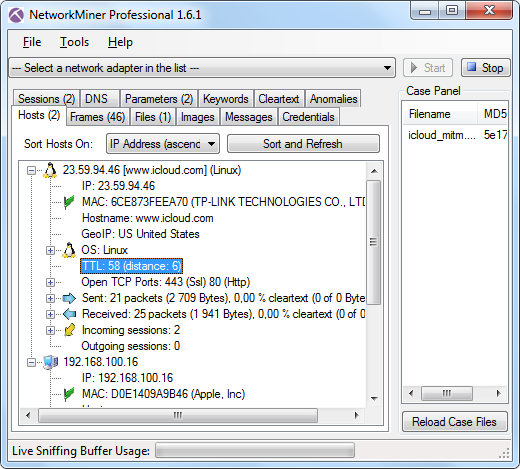
The same PCAP file also contains packets from the same IP address on TCP port 80, which have traveled 11 hops (IP TTL 53). We therefore assume that only traffic to TCP port 443 is being MITM'ed.
This TTL analysis also matches various TCP traceroutes we've seen to the MITM'ed iCloud SSL service on 23.59.94.46:443.
My traceroute [v0.85]mtr TCP 443 traceroute to 23.59.94.46 (source: http://pastebin.com/8Y6ZwfzG)
siyanmao-k29 (0.0.0.0) Sat Oct 18 19:26:07 2014
Host Loss% Snt Last Avg Best Wrst StDev
1. 192.168.1.1 0.0% 17 0.6 0.7 0.6 0.8 0.0
2. ------------- 0.0% 16 2.8 2.6 1.7 3.3 0.3
3. ------------- 0.0% 16 2.0 2.2 1.4 4.0 0.4
4. ???
5. 119.145.47.78 0.0% 16 6.4 7.7 4.3 27.0 5.2
183.56.65.54
183.56.65.50
119.145.47.74
121.34.242.250
121.34.242.138
6. 23.59.94.46 25.0% 16 168.5 171.4 166.8 201.3 9.4
The mtr TCP traceroute above indicates that MITM attacks are performed in AS4134 (China Telecom).
bearice@Bearice-Mac-Air-Haswell ~tcptraceroute to 23.59.94.46 443 (source: bearice on GitHub)
%tcptraceroute 23.59.94.46 443
Selected device en0, address 192.168.100.16, port 52406 for outgoing packets
Tracing the path to 23.59.94.46 on TCP port 443 (https), 30 hops max
1 192.168.100.254 1.737 ms 0.793 ms 0.798 ms
2 111.192.144.1 2.893 ms 2.967 ms 2.422 ms
3 61.51.246.25 2.913 ms 2.893 ms 3.968 ms
4 124.65.61.157 4.824 ms 2.658 ms 3.902 ms
5 202.96.12.9 3.626 ms 6.532 ms 3.794 ms
6 219.158.96.54 27.539 ms 26.821 ms 27.661 ms
7 a23-59-94-46.deploy.static.akamaitechnologies.com (23.59.94.46) [open] 30.064 ms 29.899 ms 30.126 ms
The tcptraceroute above indicates that MITM attacks are also performed in AS4837 (China Unicom).
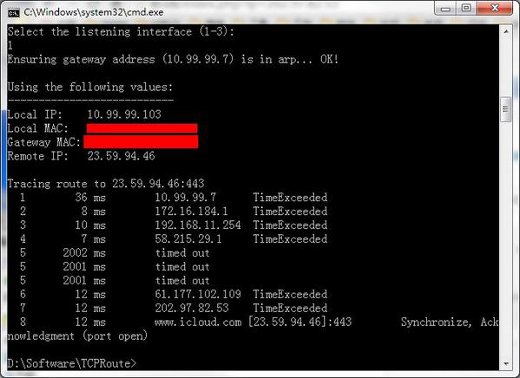
Tcproute traceroute to 23.59.94.46 on TCP 443 (source: @chenshaoju)
The Tcproute screenshot above shows that also CHINANET backbone network (China Telecom) seems to be used to carry out the MITM attacks.
Judging from these TCP traceroutes the MITM attacks seem to be taking place at several different locations rather centrally in the Chinese Internet infrastructure. To be more specific, it appears as if the MITM attacks are being performed on backbone networks belonging to China Telecom (CHINANET) as well as China Unicom.
UPDATE (October 22)
A vulnerability notice (CVE-2014-4449) has now been published, where Apple confirm that fake SSL certificates (like the Chinese fake one) were not verified by Apple iOS before 8.1. Apple released the first details about this vulnerability just a few hours after this blog post was published. Here's the text from the CVE description:
iCloud Data Access in Apple iOS before 8.1 does not verify X.509 certificates from TLS servers, which allows man-in-the-middle attackers to spoof servers and obtain sensitive information via a crafted certificate.This means that the Chinese MITM of iCloud could potentially have revealed a significant number of iCloud credentials as well as private data (images, videos, documents etc) to the attackers. Or, as @Exploit_This tweeted: "So china wants our nudes?"
Posted by Erik Hjelmvik on Monday, 20 October 2014 13:35:00 (UTC/GMT)
Tags: #Netresec #PCAP #GFW #China #PcapNG #MITM #NetworkMiner #AS4837 #AS4134



