Verifying Chinese MITM of Yahoo
 GreatFire.org sent out a tweet yesterday saying that
“Yahoo appears to under Man-in-the-middle attack in China. 3rd case of country-wide MITM, after Google, Github”.
GreatFire.org sent out a tweet yesterday saying that
“Yahoo appears to under Man-in-the-middle attack in China. 3rd case of country-wide MITM, after Google, Github”.
Mashable later ran a story called “China Appears to Attack Yahoo in Latest Censorship of Hong Kong Protests”, where Lorenzo Franceschi-Bicchierai write:
In what's almost unprecedented, China appears to be targeting Yahoo with what's called a "man-in-the-middle attack." With such an attack, connections to Yahoo.com, which are normally encrypted, would be vulnerable to snooping, and Chinese censors could also block search terms or specific Yahoo links with the goal of preventing Chinese netizens from accessing information about the protests in Hong Kong.
In this blog post we verify that there is an ongoing Man-in-the-Middle (MITM) attack by analyzing two different packet capture files.
| Capture Location | Capture Date | Filename | MD5 |
|---|---|---|---|
| Wuxi, China | 2014-09-30 10:15 (UTC) | Yahoo.pcapng | 5633a0cce5955b44 18189fe3fd27847d |
| Zhengzhou, China | 2014-09-30 11:35 (UTC) | YahooMITM.pcapng | 722ca9b7837416ef 2391b48edd20d24e |
Both PCAP files were created with Wireshark/dumpcap using a capture filter of “host 202.43.192.109”, which is the IP address that was reported to be MITM'ed by the Great Firewall of China (GFW). This IP address is located in Hong Kong and is used by Yahoo to host www.yahoo.com, hk.yahoo.com etc. for users in this part of Asia.
Time-To-Live (TTL) Analysis
We estimate the distance between the end users and the Yahoo server in Hong Kong to be at least 10 router hops. However, the IP packets coming back to the users have IP TTL values of 58 (Wuxi) and 57 (Zhengzhou). This implies that the MITM is performed somewhere in China, just 6 or 7 router hops away from the users. This is consistent with what we've observed in previous MITM attacks performed by China against GitHub and Google.
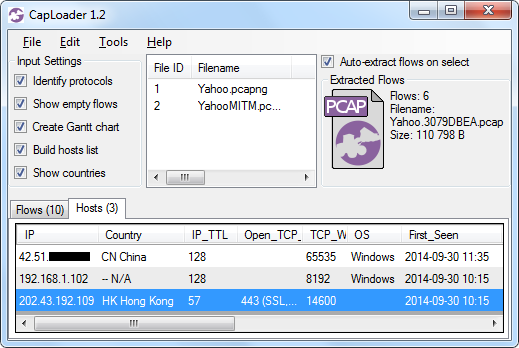
IMAGE: Hosts tab in CapLoader showing TTL 57 for hk.yahoo.com:443
X.509 Certificate Analysis
We have extracted a X.509 certificate from one of the PcapNG files to a .cer file using NetworkMiner. This SSL certificate is available for download here.
$ openssl x509 -inform DER -in yahoo.com.cer -noout -issuer -subject -startdate -enddate -fingerprint
issuer= /C=cn/O=yahoo.com/CN=yahoo.com
subject= /C=cn/O=yahoo.com/CN=yahoo.com
notBefore=Sep 23 11:30:17 2014 GMT
notAfter=Sep 23 11:30:17 2015 GMT
SHA1 Fingerprint=22:90:C3:11:EA:0F:3F:57:E0:6D:F4:5B:69:8E:18:E8:28:E5:9B:C3
The certificate is a self signed certificate for “yahoo.com”. The fact that the MITM uses a self signed certificate makes the attack easily detectable even for the non-technical user, since the web browser will typically display a warning about the site not being trusted.
Some may think it's odd that China can't forge a properly signed certificate for their SSL MITM attack. However, they've used very similar self signed certificates also in their previous MITM attacks against GitHub and Google. The purpose of GFW (a.k.a. “Golden Shield”) is to censor the Internet, so the primary goal with this MITM attack isn't to covertly spy on Chinese Yahoo searches. Regardless if the end users notice the MITM or not, a self signed X.509 cert is enough in order to see what they are searching for and “kill” their connection to Yahoo when queries like “Umbrella Revolution” and “Tiananmen Square Protests” are observed.
Posted by Erik Hjelmvik on Wednesday, 01 October 2014 21:55:00 (UTC/GMT)


