Erik Hjelmvik
,
Sunday, 23 October 2011 16:24:00 (UTC/GMT)

The “-f” switch can now be used to force RawCap to immediately flush sniffed packets to disk.
I've received multiple emails from RawCap users who run into problems when they want to look at a pcap file from RawCap
without terminating the program.
What usually happens in this case is that the output pcap file will be empty until they terminate RawCap with “Ctrl-C”.
The reason for this is that RawCap has a 1MB data buffer, which is used in order to maximize performance by reducing unnecessary disk operations.
RawCap will therefore not write any data to disk until it is terminated or has filled the buffer with 1MB of network traffic.
We've now released a new version (1.4.0.0) of RawCap in order to solve the needs of these users.
The new version supports WriteThrough,
which forces the data to be written directly to disk without being buffered.
The automatic flushing functionality is enabled by supplying the “-f” switch from the command line when launching RawCap.
There is, however, one downside with the new version of RawCap; the size of RawCap.exe has increased from 17kB to 18kB.
Sorry for that fellow minimalists... ;)
Here is an example command showing how to sniff traffic from localhost with automatic flushing (i.e. no buffer):
RawCap.exe -f 127.0.0.1 LiveLoopback.pcap
Happy live sniffing!
Posted by Erik Hjelmvik on Sunday, 23 October 2011 16:24:00 (UTC/GMT)
Tags: #Netresec
#RawCap
#loopback
#PCAP
Short URL:
https://netresec.com/?b=11A24E0
Erik Hjelmvik
,
Thursday, 13 October 2011 16:51:00 (UTC/GMT)
UPDATE :
We no longer recommend running NetworkMiner under Wine, please see our blog post on How To install NetworkMiner in Linux instead.
Joshua Smith has written a great blog post on toastresearch.com
about how to get NetworkMiner running on BackTrack Linux.
C. S. Lee (a.k.a. geek00l) has also written a blog post a couple of years ago explaining
how to install NetworkMiner on Ubuntu Linux.
Unfortunately both these blog posts point to URLs with old versions of NetworkMiner
(now that version 1.1 is released).
I'm therefore posting a simple walkthrough of the required commands in order to install the latest version of NetworkMiner on an Ubuntu machine:
sudo apt-get install winetricks
winetricks corefonts dotnet20 gdiplus
cd /opt
wget www.netresec.com/?download=NetworkMiner
unzip latest
cd NetworkMiner_1-1/
wine NetworkMiner.exe
I hope this will help you get NetworkMiner running on your Ubuntu analyst station!
We will also be looking into having NetworkMiner fully compatible with mono in a future release.
This would allow you to run NetworkMiner “natively” on Linux, Mac OS X as well as BSD (OpenBSD, FreeBSD, NetBSD).
Posted by Erik Hjelmvik on Thursday, 13 October 2011 16:51:00 (UTC/GMT)
Tags: #Netresec
#Linux
#Wine
#Ubuntu
Short URL:
https://netresec.com/?b=11A3324
Erik Hjelmvik
,
Monday, 03 October 2011 21:54:00 (UTC/GMT)

A new feature in version 1.1 of NetworkMiner
aids the task of identifying a suspect user by extracting information about browser language and screen resolution sent to
Google Analytics.
Google Analytics is the most popular website statistics service
and is used by roughly half of all websites on the Internet.
This means that a user surfing the Internet will most likely send data to Google Analytics.
The data being sent to Google's servers include Flash version, screen resolution, color depth and browser language.
This data isn't very intrusive on the privacy of Internet users, but can still provide some value to an investigator
who wants to gain more information about a computer with a particular IP address as well as the user of that computer.
The browser language can, for example, be used to gain more information about the nationality of a particular user.
In the screenshot below we can see that the user was running a web browser with Swedish language
(look at “Browser Language” under “Host Details” and you'll see “sv” for
“svenska”).
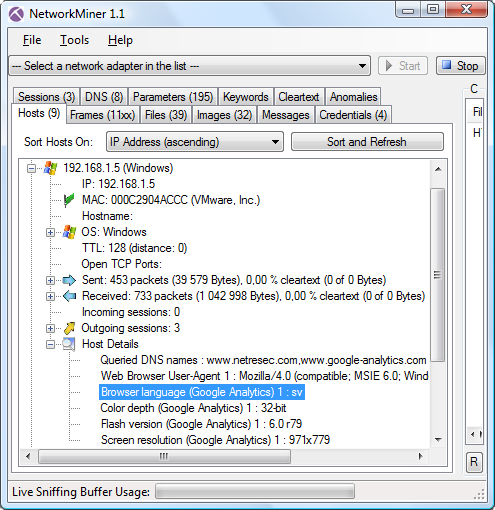
Observant blog readers might also notice the odd screen resolution used by this particular user,
namely “971x779”. The most common reason for having such an odd resolutions is that the web browser is run in a virtual machine
(likely VMware with VMware tools installed). This assumption is in this case enforced by the fact that the MAC address starts with 000c29,
which is a VMware OUI.
The MAC address will, however, not be visible as soon as the network traffic from the suspect's computer passes the first router hop.
The screen resolution parameter sent to Google will, on the other hand, be visible all the way from the suspect's computer to
google-analytics.com.
Information like this about the screen resolution can be used as evidence for an investigator in order to better prove that a particular
computer was being used from a particular IP address at some specific point in time.
More information about Google Analytics can be found here:
http://www.christopher-parsons.com/blog/privacy/google-analytics-privacy-and-legalese/
Posted by Erik Hjelmvik on Monday, 03 October 2011 21:54:00 (UTC/GMT)
Tags:
Short URL:
https://netresec.com/?b=11ADE66







