Fast analysis of large pcap files with CapLoader

Are you working with large pcap files and need to see the “whole picture” while still being able to quickly drill down to individual packets for a TCP or UDP flow? Then this is your lucky day, since we at Netresec are releasing our new tool CapLoader today!
Here are the main features of CapLoader:
- Fast loading of multi-gigabyte PCAP files (1 GB loads in less than 2 minutes on a standard PC and even faster on multi-core machines).
- GUI presentation of all TCP and UDP flows in the loaded PCAP files.
- Automatic identification of application layer protocols without relying on port numbers.
- Extremely fast drill-down functionality to open packets from one or multiple selected flows.
- Possibility to export packets from selected flows to a new PCAP file or directly open them in external tools like Wireshark and NetworkMiner.
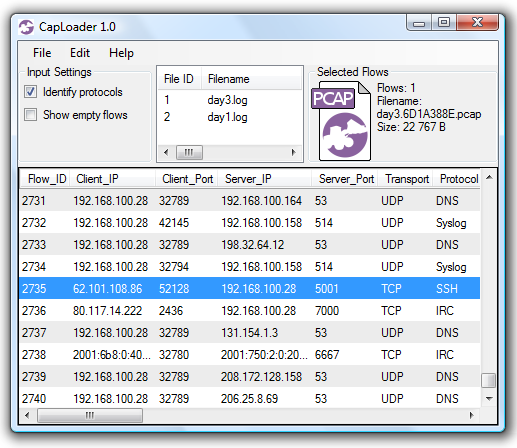
CapLoader with files from Honeynet SOTM 28 loaded. The application layer protocol from the rootkit backdoor on TCP 5001 is automatically identified as "SSH".
The typical process of working with CapLoader is:
-
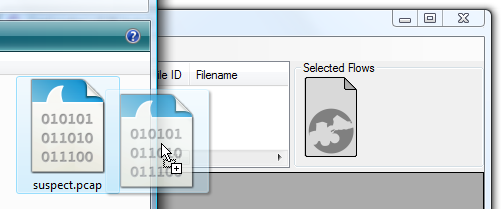
Open one or multiple pcap files, typically by drag-and-dropping them onto the CapLoader GUI.
-
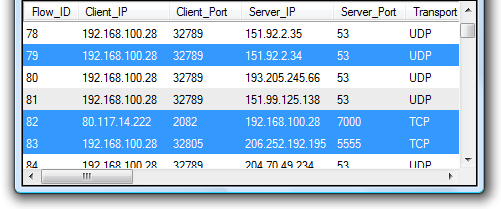
Mark the flows of interest.
-
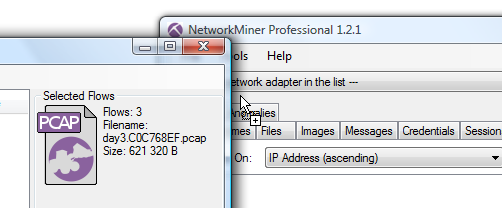
Double click the PCAP icon to open the selected sessions in your default pcap parser (typically Wireshark) or better yet,
do drag-and-drop from the PCAP icon to your favorite packet analyzer.
In short, CapLoader will significantly speed up the analysis process of large network captures while also empowering analysts with a unique protocol identification ability. We at Netresec see CapLoader as the perfect tool for everyone who want to perform analysis on “big data” network captures.
More information about CapLoader is available on caploader.com.
Posted by Erik Hjelmvik on Monday, 02 April 2012 19:55:00 (UTC/GMT)
Tags: #Netresec #CapLoader #Fast #Big Data #PCAP #Flow



