PolarProxy Released
I’m very proud to announce the release of PolarProxy today! PolarProxy is a transparent TLS proxy that decrypts and re-encrypts TLS traffic while also generating a PCAP file containing the decrypted traffic.
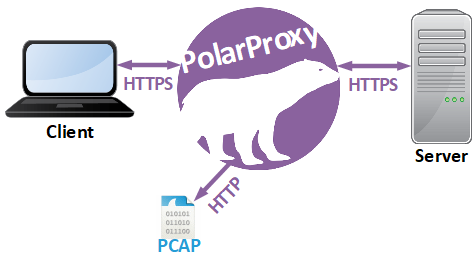
PolarProxy enables you to do lots of things that have previously been impossible, or at least very complex, such as:
- Analyzing HTTP/2 traffic without an SSLKEYLOGFILE
-
Viewing decrypted HTTPS traffic in real-time using Wireshark
PolarProxy -p 10443,80,443 -w - | wireshark -i - -k
-
Replaying decrypted traffic to an internal or external interface using
tcpreplayPolarProxy -p 10443,80,443 -w - | tcpreplay -i eth1 -
- Forwarding of decrypted traffic to a NIDS (see tcpreplay command above)
-
Extracting DNS queries and replies from
DNS-over-TLS (DoT) or
DNS-over-HTTPS (DoH) traffic
PolarProxy -p 853,53 -p 443,80 -w dns.pcap
-
Extracting email traffic from SMTPS, POP3S or IMAPS
PolarProxy -p 465,25 -p 995,110 -p 993,143 -w emails.pcap
Here is an example PCAP file generated by PolarProxy:
https://media.netresec.com/pcap/polarproxy-demo.pcap
This capture files contains HTTP, WebSocket and HTTP/2 packets to Mozilla, Google and Twitter that would otherwise have been encrypted with TLS.
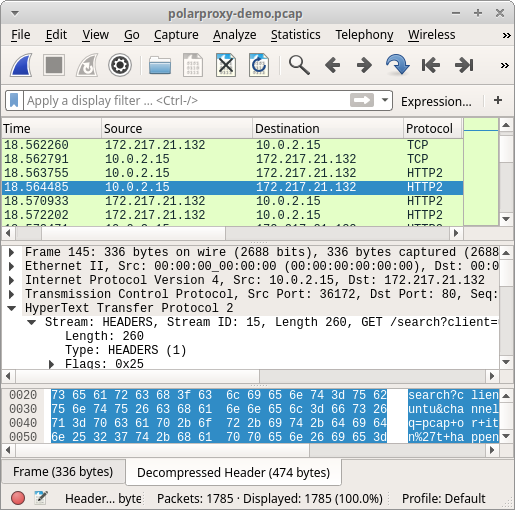
Image: HTTP/2 traffic from PolarProxy opened in Wireshark
Now, head over to our PolarProxy page and try it for yourself (it’s free)!
Posted by Erik Hjelmvik on Friday, 21 June 2019 06:00:00 (UTC/GMT)
Tags: #PolarProxy #PCAP #NIDS #IDS #http2 #HTTP/2 #SSLKEYLOGFILE #Wireshark #tcpreplay #DoH #SMTPS #IMAPS #TLS #SSL



