Erik Hjelmvik
,
Monday, 15 August 2022 08:05:00 (UTC/GMT)

PCAP-over-IP is a method for reading a PCAP stream, which contains captured network traffic, through a TCP socket instead of reading the packets from a PCAP file.
A simple way to create a PCAP-over-IP server is to simply read a PCAP file into a netcat listener, like this:
nc -l 57012 < sniffed.pcap
The packets in “sniffed.pcap” can then be read remotely using PCAP-over-IP, for example with tshark like this (replace 192.168.1.2 with the IP of the netcat listener):
nc 192.168.1.2 57012 | tshark -r -
But there’s an even simpler way to read PCAP-over-IP with Wireshark and tshark, which doesn’t require netcat.
wireshark -k -i TCP@192.168.1.2:57012
tshark -i TCP@192.168.1.2:57012
The Wireshark name for this input method is “TCP socket” pipe interface, which is available in Linux, Windows and macOS builds of Wireshark as well as tshark.
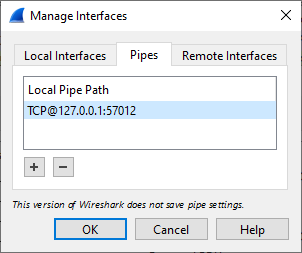
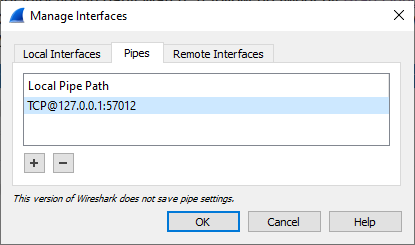
It is also possible to add a PCAP-over-IP interface from Wireshark's GUI. Open Capture/Options, Manage Interfaces, Pipes Tab and then enter a Local Pipe Path such as TCP@127.0.0.1:57012 and click OK. This setting will disappear when you close Wireshark though, since pipe settings don't get saved.
Live Remote Sniffing
Sniffed traffic can be read remotely over PCAP-over-IP in real-time simply by forwarding a PCAP stream with captured packets to netcat like this:
tcpdump -U -w - not tcp port 57012 | nc -l 57012
dumpcap -P -f "not tcp port 57012" -w - | nc -l 57012
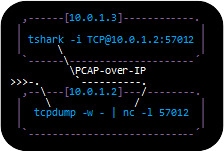
Tcpdump is not available for Windows, but dumpcap is since it is included with Wireshark.
Note how TCP port 57012 is purposely filtered out using BPF when capturing in order to avoid a snowball effect, where the PCAP-over-IP traffic otherwise gets sniffed and re-transmitted through the PCAP-over-IP stream, which again gets sniffed etc.
A more sophisticated setup would be to let the service listening on TCP port 57012 spawn the sniffer process, like this:
nc.traditional -l -p 57012 -c "tcpdump -U -w - not port 57012"
Or even better, let the listening service reuse port 57012 to allow multiple incoming PCAP-over-IP connections.
socat TCP-LISTEN:57012,reuseaddr,fork EXEC:"tcpdump -U -w - not port 57012"
Reading PCAP-over-IP with NetworkMiner
We added PCAP-over-IP support to NetworkMiner in 2011 as part of NetworkMiner 1.1, which was actually one year before the TCP socket sniffing feature was included in Wireshark.
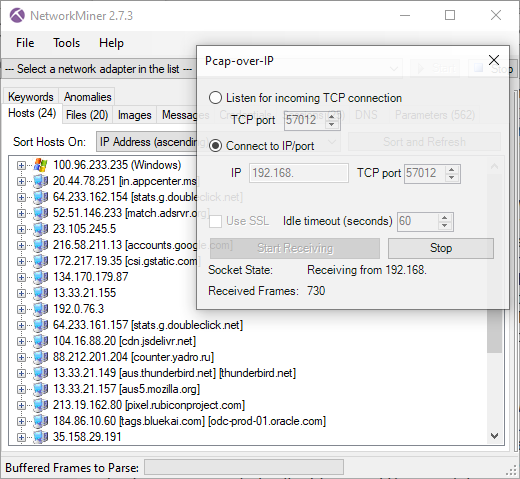
Image: Live remote sniffing with NetworkMiner 2.7.3 using PCAP-over-IP
NetworkMiner can also be configured to listen for incoming PCAP-over-IP connections, in which case the sniffer must connect to the machine running NetworkMiner like this:
tcpdump -U -w - not tcp port 57012 | nc 192.168.1.3 57012
This PCAP-over-IP feature is actually the recommended method for doing real-time analysis of live network traffic when running NetworkMiner in Linux or macOS, because NetworkMiner’s regular sniffing methods are not available on those platforms.
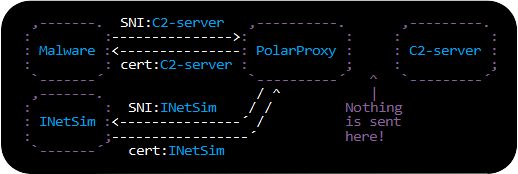
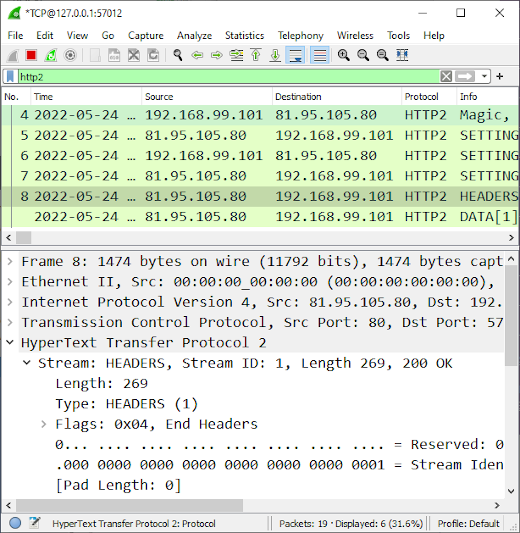
Reading Decrypted TLS Traffic from PolarProxy

One of the most powerful use-cases for PCAP-over-IP is to read decrypted TLS traffic from PolarProxy. When PolarProxy is launched with the argument “--pcapoverip 57012” it starts a listener on TCP port 57012, which listens for incoming connections and pushes a real-time PCAP stream of decrypted TLS traffic to each client that connects. PolarProxy can also make active outgoing PCAP-over-IP connections to a specific IP address and port if the “--pcapoveripconnect <host>:<port>” argument is provided.
In the video PolarProxy in Windows Sandbox I demonstrate how decrypted TLS traffic can be viewed in NetworkMiner in real-time with help of PCAP-over-IP. PolarProxy’s PCAP-over-IP feature can also be used to
read decrypted TLS traffic from PolarProxy with Wireshark as well as to send decrypted TLS traffic from PolarProxy to Arkime (aka Moloch).
Replaying PCAP-over-IP to an Interface
There are lots of great network monitoring products and intrusion detection systems that don’t come with a built-in PCAP-over-IP implementation, such as Suricata, Zeek, Security Onion and Packetbeat, just to mention a few. These products would greatly benefit from having access to the decrypted TLS traffic that PolarProxy can provide. Luckily we can use netcat and tcpreplay to replay packets from a PCAP-over-IP stream to a network interface like this:
nc localhost 57012 | tcpreplay -i eth0 -t -
But for permanent installations we recommend creating a dedicated dummy interface, to which the traffic gets replayed and sniffed, and then deploy a systemd service that performs the replay operation. See our blog post Sniffing Decrypted TLS Traffic with Security Onion for an example on how to deploy such a systemd service. In that blog post we show how decrypted TLS traffic from PolarProxy can be replayed to a local interface on a Security Onion machine, which is being monitored by Suricata and Zeek.
Nils Hanke has also compiled a detailed documentation on how decrypted TLS packets from PolarProxy can be replayed to Packetbeat and Suricata with help of tcpreplay.
In these setups netcat and tcpreplay act as a generic glue between a PCAP-over-IP service and tools that can sniff packets on a network interface, but there are a few drawbacks with this approach.
One drawback is that tcpreplay requires root privileges in order to replay packets to an interface. Another drawback is that extra complexity is added to the solution and two additional single point of failures are introduced (i.e. netcat and tcpreplay). Finally, replaying packets to a network interface increases the risk of packet drops. We therefore hope to see built-in PCAP-over-IP implementations in more network monitoring solutions in the future!
FAQ for PCAP-over-IP
Q: Why is it called “PCAP-over-IP” and not “PCAP-over-TCP”?
Good question, we actually don’t know since we didn’t come up with the name. But in theory it would probably be feasible to read a PCAP stream over UDP or SCTP as well.
Q: What is the standard port for PCAP-over-IP?
There is no official port registered with IANA for PCAP-over-IP, but we’ve been using TCP 57012 as the default port for PCAP-over-IP since 2011. The Wireshark implementation, on the other hand, uses TCP port 19000 as the default value.
Q: Which software comes with built-in PCAP-over-IP servers or clients?
The ones we know of are: Arkime, NetworkMiner, PolarProxy, tshark and Wireshark.
There is also a PCAP-over-IP plugin for Zeek (see update below).
Q: Is there some way to encrypt the PCAP-over-IP transmissions?
Yes, we recommend encrypting PCAP-over-IP sessions with TLS when they are transmitted across a non-trusted network. NetworkMiner’s PCAP-over-IP implementation comes with a “Use SSL” checkbox, which can be used to receive “PCAP-over-TLS”. You can replace netcat with socat or ncat in order to establish a TLS encrypted connection to NetworkMiner.
Q: Is there a tool that can aggregate multiple PCAP-over-IP streams into one?
No, none that we’re aware of. However, multiple PCAP-over-IP streams can be merged into one by specifying multiple PCAP-over-IP interfaces in dumpcap and then forwarding that output to a netcat listener, like this:
dumpcap -i TCP@10.1.2.3:57012 -i TCP@10.4.5.6:57012 -w - | editcap -F pcap - - | nc -l 57012
Update 2023-04-13
Erich Nahum has published zeek-pcapovertcp-plugin, which brings native PCAP-over-IP support to Zeek.
Erich's plugin can be installed as a zeek package through zkg.
zkg install zeek-pcapovertcp-plugin
After installing the plugin, a command like this reads a PCAP stream from a remote source:
zeek -i pcapovertcp::192.168.1.2:57012
Update 2025-11-27
Fox-IT have released pcap-broker, which can be used to distribute PCAP-over-IP to multiple clients.
You can build and run pcap-broker as a Docker container like this:
git clone https://github.com/fox-it/pcap-broker.git
docker build -t pcap-broker pcap-broker/
docker run -it --net=host pcap-broker -cmd "tcpdump -U -w - not port 57012" -listen localhost:57012
Posted by Erik Hjelmvik on Monday, 15 August 2022 08:05:00 (UTC/GMT)
Tags:
#PCAP-over-IP
#PCAP
#tcpdump
#Wireshark
#tshark
#NetworkMiner
#PolarProxy
#Suricata
#Zeek
#Arkime
#tcpreplay
#netcat
#ASCII-art