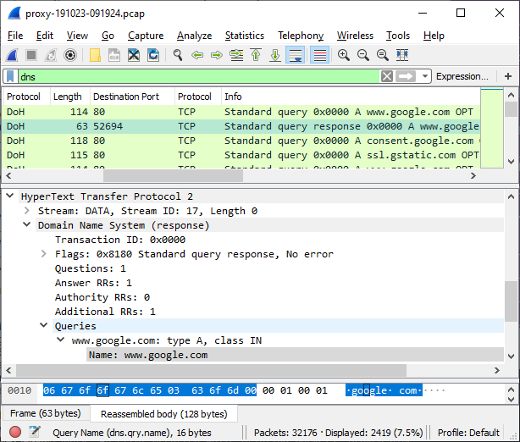
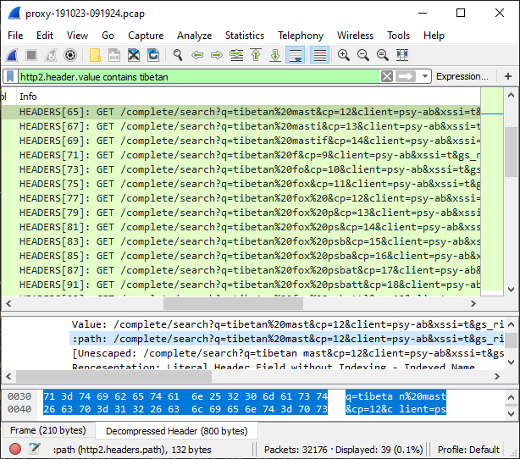
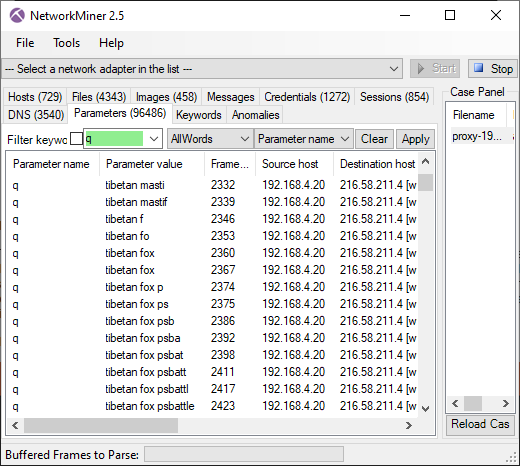
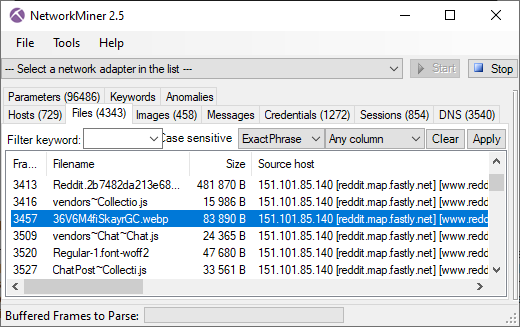
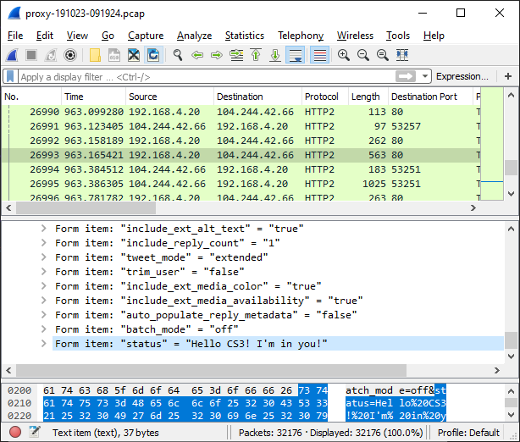
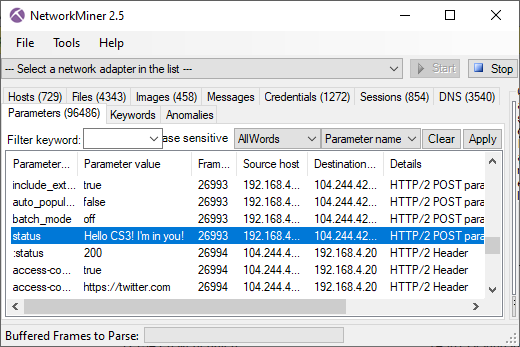
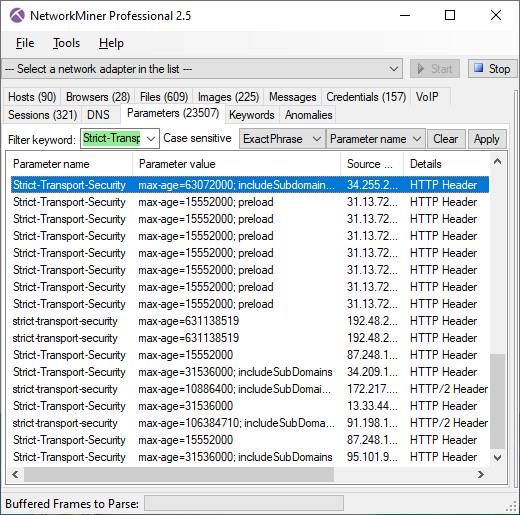
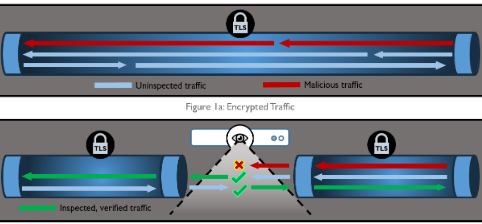
PolarProxy in Docker
Our transparent TLS proxy PolarProxy is gaining lots of popularity due to how effective it is at generating decrypted PCAP files in combination with how easy it is to deploy. In this blog post we will show how to run PolarProxy in Docker.
Installation Instructions
Create a Dockerfile with the following contents:
EXPOSE 10443
EXPOSE 10080
EXPOSE 57012
RUN groupadd -g 31337 polarproxy && useradd -m -u 31337 -g polarproxy polarproxy && mkdir -p /var/log/PolarProxy /opt/polarproxy && chown polarproxy:polarproxy /var/log/PolarProxy && apt-get update && apt-get install -y curl && curl -s https://www.netresec.com/?download=PolarProxy | tar -xzf - -C /opt/polarproxy
VOLUME ["/var/log/PolarProxy/", "/home/polarproxy/"]
USER polarproxy
WORKDIR /opt/polarproxy/
ENTRYPOINT ["dotnet", "PolarProxy.dll"]
CMD ["-v", "-p", "10443,80,443", "-o", "/var/log/PolarProxy/", "--certhttp", "10080", "--pcapoverip", "0.0.0.0:57012"]
Save the Docker file as "Dockerfile" (no extension) in an empty directory and start a shell in that directory with root privileges.
Update (2024-05-02): Additional dockerfiles can now be found in https://github.com/Netresec/PolarProxy/tree/main/dockerfiles
Build the PolarProxy Docker image with:
Next, create a Docker container named "polarproxy":
It is now time to start the polarproxy container:
Verify that PolarProxy is running:
docker logs polarproxy
Try fetching PolarProxy's public root CA certificate with curl and then connect to a website over HTTPS through the proxy:
curl --insecure --connect-to www.netresec.com:443:127.0.0.1:10443 https://www.netresec.com/
curl --insecure --resolve www.netresec.com:443:127.0.0.1 https://www.netresec.com/
Redirect HTTPS and Trust the Root CA
You can now redirect outgoing TCP 443 traffic from your network to your Docker host. Review the "Routing HTTPS Traffic to the Proxy" section on the PolarProxy page for recommendations on how to redirect outgoing traffic to PolarProxy.
Finally, configure the operating system, browsers and other applications that will get their TLS traffic proxied by PolarProxy to trust the root CA of the PolarProxy service running in your Docker container. Follow the steps in the "Trusting the PolarProxy root CA" section of the PolarProxy documentation in order to install the root cert.
Docker Volumes
The Docker file we used in this blog post defines two volumes. The first volume is mounted on "/var/log/PolarProxy" in the container, which is where the decrypted network traffic will be stored as hourly rotated PCAP files. The second volume is the polarproxy home directory, under which PolarProxy will store its private root CA certificate.
The volumes are typically located under "/var/lib/docker/volumes" on the Docker host's file system. You can find the exact path by running:
docker volume inspect <VOLUME_NAME>
Or use find to list *.pcap files in the Docker volumes directory:
/var/lib/docker/volumes/7ebb3f56fd4ceab96[...]/_data/proxy-201006-095937.pcap/var/lib/docker/volumes/7ebb3f56fd4ceab96[...]/_data/proxy-201006-105937.pcap/var/lib/docker/volumes/7ebb3f56fd4ceab96[...]/_data/proxy-201006-115937.pcap
The full path of your private PolarProxy Root CA certificate, which is located under "/home/polarproxy/" in the Docker container, can also be located using find:
/var/lib/docker/volumes/dcabbbac10e1b1461[...]/_data/.local/share/PolarProxy/e249f9c497d7b5c41339f153a31eda1c.p12
We recommend reusing the "/home/polarproxy/" volume, when deploying new PolarProxy instances or upgrading to a new version of PolarProxy, in order to avoid having to re-configure clients to trust a new root CA every time a new PolarProxy container is created.
PolarProxy in Docker on ARM Linux
PolarProxy can also run on ARM Linux installations, such as a Raspberry Pi. However, the Dockerfile must be modified slightly in order to do so.
Don't know if you're running a 32-bit or 64-bit OS? Run "uname -m" and check if the output says "armv7*" (arm32), "armv8*" (arm64) or "aarch64" (arm64).
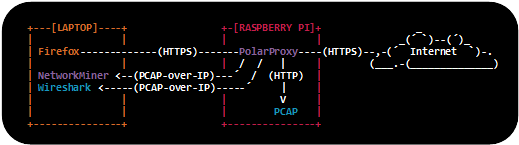
See our blog post "Raspberry PI WiFi Access Point with TLS Inspection" for more details about deploying PolarProxy on a Raspberry Pi (without Docker).
Credits
We'd like to thank Jonas Lejon for contacting us back in February about the work he had done to get PolarProxy running in Docker. We used Jonas' work as a starting point when building the installation instructions in this how-to guide.
We also want to thank Erik Ahlström for providing valuable feedback on the instructions in this guide.
ʕ•ᴥ•ʔ + 🐳 = 💜
Posted by Erik Hjelmvik on Wednesday, 07 October 2020 08:09:00 (UTC/GMT)
Tags: #PolarProxy #Docker #TLS #HTTPS #Proxy #TLSI #Dockerfile #curl #x509 #X.509 #PCAP #DNAT #container #DNAT #arm32 #arm64 #AArch64 #PCAP-over-IP #pcapoverip