Decoding malware C2 with CyberChef
This video tutorial demonstrates how malware XOR encrypted and obfuscated C2 traffic can be decoded with CyberChef.
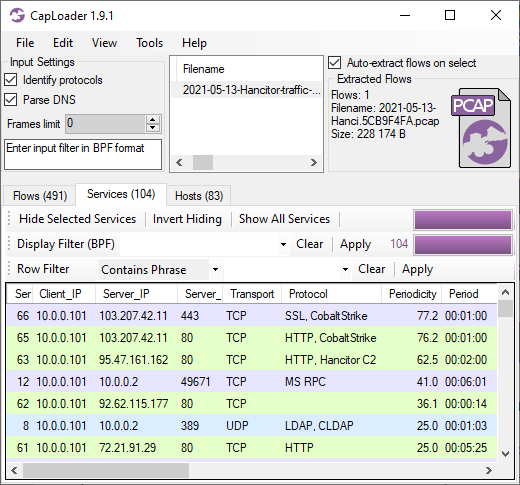
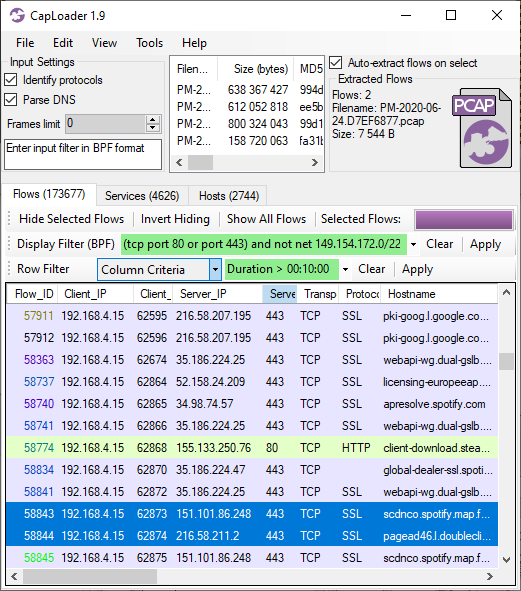
The analyzed PCAP files can be downloaded from malware-traffic-analysis.net.
CyberChef recipe to decode the reverse shell traffic to 103.27.157.146:4444:
XOR({'option':'Hex','string':'62'},'Standard',false)
Find_/_Replace({'option':'Regex','string':'\\r'},'',true,false,true,false)
From_HTML_Entity()
Decoded data from first "key007" reverse shell session to 103.27.157.146:4444:
Authentication successful
furtheringthemagic.com
net group "domain computers" /domain
The request will be processed at a domain controller for domain furtheringthemagic.com.
Group name Domain Computers
Comment All workstations and servers joined to the domain
Members
-------------------------------------------------------------------------------
DESKTOP-G71S4PF$
The command completed successfully.
CyberChef recipe to decode obfuscated PowerShell payload from malicious finger service on 64.190.113.206:79:
Pad_lines('End',5,',6044')
Subtract('Comma')
From_Charcode('Space',10)
Update 2026-01-21
Our classification of the final payload has been updated from AsyncRAT to GhostWeaver thanks to feedback from Don Pasci. Don referenced a writeup by Recorded Future's Insikt Group, called Uncovering MintsLoader With Recorded Future Malware Intelligence Hunting, which states the following:
GhostWeaver has periodically been misclassified as AsyncRAT. [...] GhostWeaver and AsyncRAT share certain characteristics within their self-signed X.509 certificates, such as identical expiration dates and serial number lengths; however, these similarities may simply reflect common certificate-generation methods rather than meaningful operational overlap.
We also believe that some of the PowerShell related traffic was caused by MintsLoader.
IOC List
- 103.27.157.146:4444 (unknown "key007" reverse shell)
- 64.190.113.206:79 (finger)
- checkifhuman[.]top (finger)
- ey267te[.]top (MintsLoader)
- 64.52.80.153:80 (MintsLoader)
- 173.232.146.62:25658 (
AsyncRATGhostWeaver) - 08kcbghk807qtl9[.]fun:25658 (
AsyncRATGhostWeaver)
Network Forensics Training
Check out our network forensic trainings if you want to learn more about decoding malware C2 traffic. I'm teaching a live online Network Forensics for Incident Response class on February 23-26.
Posted by Erik Hjelmvik on Tuesday, 20 January 2026 12:10:00 (UTC/GMT)
Tags: #Netresec #CyberChef #XOR #PCAP #CapLoader #PowerShell #Video #videotutorial







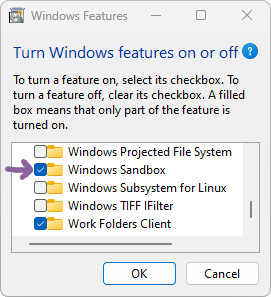 Follow these steps to install Windows Sandbox:
Follow these steps to install Windows Sandbox: