
CapLoader
CapLoader is a Windows tool designed to handle large amounts of captured network traffic. CapLoader performs indexing of PCAP/PcapNG files and visualizes their contents as a list of TCP and UDP flows. Users can select the flows of interest and quickly filter out those packets from the loaded PCAP files. Sending the selected flows/packets to a packet analyzer tool like Wireshark or NetworkMiner is then just a mouse click away.
CapLoader is the ideal tool if you're working with large PCAP files or datasets consisting of many PCAP files. The contents of individual flows can be exported to tools like Wireshark and NetworkMiner in just a matter of seconds after having loaded one or multiple large PCAP files.
Next live online network forensics training: February 23-26, 2026Video Tutorials
Video tutorial from our blog post "Analyzing Kelihos SPAM in CapLoader and NetworkMiner".
Video tutorial from our blog post "Hunting for Cobalt Strike in PCAP".
Video tutorial from our blog post "Detecting Cobalt Strike and Hancitor traffic in PCAP".
Usage
The typical process of working with CapLoader is:
-
Open one or multiple pcap files, typically by drag-and-dropping them onto the CapLoader GUI.
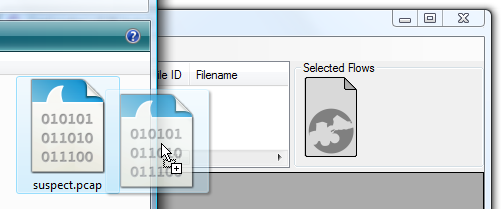
-
Select/mark the flows of interest.
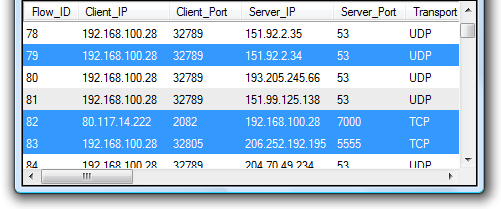
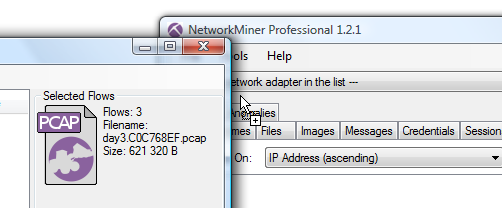
-
Double click the PCAP-icon to open the selected sessions in your default pcap parser (typically Wireshark) or better yet, do drag-and-drop from the PCAP-icon to any application you wish.
Built-in Protocol Identification
CapLoader includes the ability to identify protocols without relying on port numbers (a feature often referred to as “traffic classification”). This feature can be enabled by checking the “Identify protocols” check-box in the GUI. Loading PCAP files with the “identify protocols” feature enabled will cause the application layer protocols of the extracted flows to be identified and displayed in the flow list. Being able to identify the application layer protocol is important in order to detect what services that run on non-standard ports as well as to detect if common ports are being used to transport other protocols than what might be expected.
The dynamic protocol identification feature allows for detection of over 100 protocols and sub-protocols. The identified protocols include Skype, IRC, FTP and SSH, MS-RPC, Poison Ivy RAT as well as several P2P and CardSharing protocols.
Read our Port Independent Protocol Detection blog post for more details on the protocol detection feature built into CapLoader.
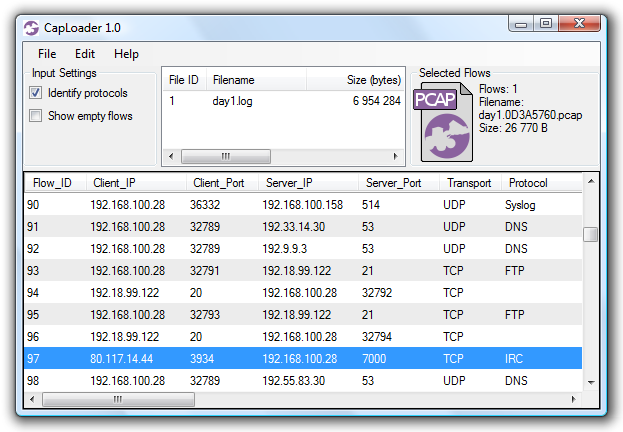
CapLoader showing port independent identification of protocols
Network Packet Carving
CapLoader has the ability to carve network packets from any file and save them in the PCAP-NG format. This fusion between memory forensics and network forensics makes it possible to extract sent and received IP frames, with complete payload, from RAM dumps as well as from raw disk images. CapLoader basically carves any TCP or UDP packet that is preceded by an IP frame (both IPv4 and IPv6 are supported).
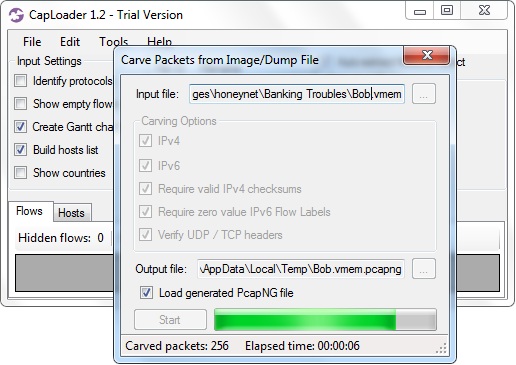
CapLoader 1.2 Carving Packets from HoneyNet Memory Image
Try or Buy CapLoader
| CapLoader Trial | CapLoader (professional edition) | |
|---|---|---|
| License Validity Period | 30 Days | 3 Years |
| Max PCAP Data Size | 5 GB | No limit |
| Reads PcapNG Files | ✅ | ✅ |
| Reads ETL Files | ✅ | ✅ |
| IPv6 Support | ✅ | ✅ |
|
Flow Transcript View
(a.k.a Follow TCP/UDP Stream) |
✅ | ✅ |
| Indexing of Flows for Fast Extraction | ✅ | ✅ |
| VXLAN Parser | ✅ | ✅ |
| Hostname extraction from DNS | ✅ | ✅ |
| Hostname extraction from TLS | ✅ | |
| Extract JA3 and JA3S | ✅ | |
| Extract JA4 fingerprints | ✅ | |
| Initial Round Trip Time calculation | ✅ | ✅ |
| Top 1M Main Domain Lookup | ✅ | |
| Top 1M FQDN Lookup | ✅ | |
|
Port Independent Protocol Identification (PIPI) |
✅ | |
| Define Protocol from Traffic | ✅ | |
| Select Similar Flows | ✅ | |
| Alert on Malicious Protocol | ✅ | |
| Alert on Port-protocol Mismatch | ✅ | |
| Alert on Periodic Connections | ✅ | ✅ |
| Offline IP-to-Country lookup | ✅ | |
| Offline IP ASN lookup | ✅ | |
| OSINT lookup of IP's and domains | ✅ | |
| Network Packet Carving | ✅ | ✅ |
| Keyword String Search | ✅ | ✅ |
| Regular Expression (regex) Search | ✅ | |
| Input Filter (BPF) | ✅ | ✅ |
| Hide Flows in GUI | ✅ | ✅ |
| Display Filter (BPF) | ✅ | ✅ |
| Keyword Filter | ✅ | ✅ |
| Select Flows from Log file | ✅ | |
| Select Flows from PCAP file | ✅ | |
| Detection of Periodic Connections | ✅ | ✅ |
| Wireshark style Coloring | ✅ | |
| Price | Free | From $ 1300 USD |
| Download Free Trial | Buy CapLoader |
Change Log
| Version | Date | Major Improvements |
|---|---|---|
| 2.0.1 | 2025-07-01 | IP lookup alert and bug fixes |
| 2.0 | 2025-06-02 | User-defined protocols from example traffic, QUIC parser, 10x faster user interface. |
| 1.9.7 | 2024-09-06 | Community ID and retransmissions columns, improved protocol detection and more decapsulated protcols. |
| 1.9.6 | 2023-11-16 | Integration with ThreatFox and JA4 fingerprints. |
| 1.9.5 | 2023-02-09 | Alerts for malicious traffic. |
| 1.9.4 | 2022-06-16 | Extraction of JA3 and JA3S hashes, Select Similar Flows and VXLAN decapsulation. |
| 1.9.3 | 2021-11-02 | Read Windows event tracing .etl files. |
| 1.9.2 | 2021-07-01 | Bug fixes. |
| 1.9.1 | 2021-05-27 | Bug fixes. |
| 1.9 | 2021-05-27 | Column Criteria filter, VLAN support in BPF and better periodicity detection. |
Dependencies
CapLoader requires Microsoft .NET Framework 4.8 to be installed.
