CapLoader 1.9.6 Released

CapLoader now detects even more malicious protocols and includes several new features such as JA4 fingerprints, API support for sharing IOCs to ThreatFox and OSINT lookups of malware families on Malpedia. The new CapLoader 1.9.6 release also comes with several improvements of the user interface, for example interactive filtering of flows and services with regular expressions.
Detection of Malware C2 Protocols
Malware authors continually keep coming up with new C2 protocols for defenders to detect. Luckily we don’t need to manually create protocol signatures for CapLoader, we only need a few examples of traffic for a protocol to generate a statistical model that CapLoader can use to detect that protocol. We call this feature Port Independent Protocol Identification (PIPI).
We’ve added support for detecting of the following protocols in this new release of CapLoader:
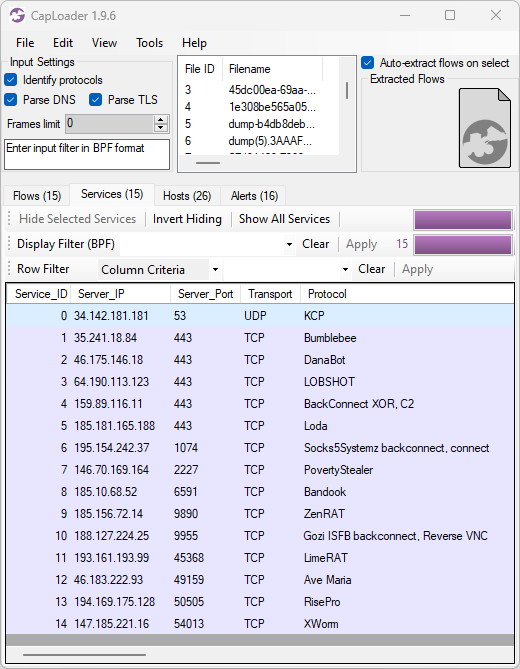
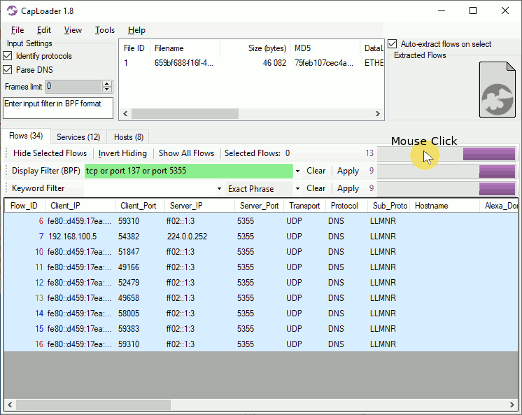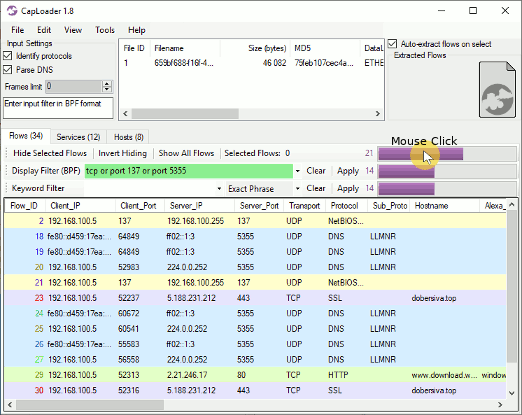
Image: Protocols identified in PCAP files with malware traffic from various sandboxes (ANY.RUN, Hybrid-Analysis, Joe Sandbox and Triage)
Our PIPI feature can also detect protocols inside of other protocols, such as Cobalt Strike, DCRat, Emotet, Formbook, Gozi ISFB, GzipLoader and Socks5Systemz which all run on top of HTTP. It is sometimes even possible to identify malicious protocols that use TLS encryption, such as AsyncRAT, Cobalt Strike, Emotet, IcedID or Remcos. However, detection of malicious TLS encrypted protocols is a difficult challenge and might be subject to false positives.
Sharing IOCs to ThreatFox
ThreatFox is a free online service for sharing indicators of compromise (IOCs) from malware. ThreatFox can be queried for a particular malware family, such as RedLine Stealer, and it’ll return a list of URLs, domain names and IP:port pairs used for C2 communication or payload delivery for that malware. You can also query for a domain or IP address to see if it’s a known C2 address of any malware or botnet.
CapLoader has supported OSINT lookup of IP addresses and domains on ThreatFox since the release of version 1.9, but with this release we also add the ability to contribute by sharing IOCs with the infosec community. All you need to do is to enter your ThreatFox API-key in CapLoader’s settings, then right-click a flow, service or alert and select “Submit to ThreatFox”.
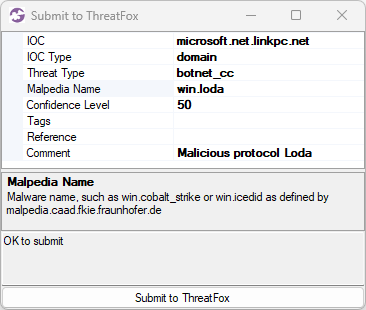
Image: Submission of microsoft.net.linkpc[.]net to ThreatFox
If the right-clicked item is an alert for a “Malicious protocol” then CapLoader will automatically populate the Mapledia Name field, as shown in the screenshot (win.loda).
TLS Client Fingerprinting with JA4
John Althouse announced the new JA4+ fingerprint methods a couple of months ago on the FoxIO blog. In short JA4+ is a suite of methods designed to fingerprint implementations of a specific set of protocols, including TLS, HTTP and SSH. As you’ve probably guessed JA4+ is a successor to the JA3 and JA3S hashes that we’ve learned to love (we added JA3 fingerprinting to NetworkMiner in 2019).
Most of the fingerprinting methods in the JA4+ suite are patent pending except for the TLS client fingerprinting method “JA4”, which FoxIO does not have patent claims and is not planning to pursue patent coverage for. We have therefore built a JA4 fingerprinting engine that we’ve included in this CapLoader release. Future releases of NetworkMiner will hopefully also include our JA4 fingerprinting engine.
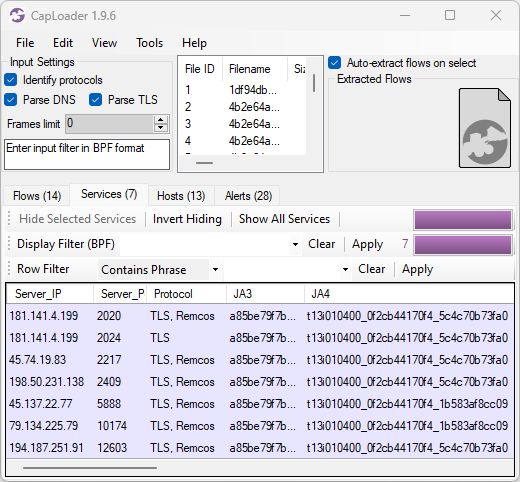
Image: JA3 and JA4 hashes of Remcos C2 traffic
JA4 is similar to JA3 in many ways, but one essential difference is that JA4 fingerprints are something of a fuzzy hash of the client’s handshake rather than a MD5 hash of the raw fingerprint. JA3’s use of MD5 hashing has received criticism, for example in academic literature, partly due to the inability to see if two JA3 hashes have similar TLS handshakes.
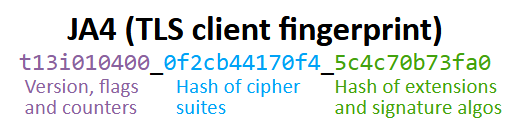
JA4 does use hashes, but instead of just being one big hash it breaks the fingerprint into three separate sections; where the first section is used in its raw (non-hashed) format and the other two sections are hashed separately. Thus, an update of a TLS implementation, which only adds one additional cipher, will increment the cipher counter in the first section of the JA4 fingerprint by one and the ciphers hash (second section) will get a new value. The hash in the last section will remain intact.
In the previous CapLoader screenshot with Remcos C2 traffic we see TLS handshakes that have the same JA3 hash (a85be79f7b569f1df5e6087b69deb493) but the JA4 fingerprints have different values (t13i010400_0f2cb44170f4_5c4c70b73fa0 and t13i010400_0f2cb44170f4_1b583af8cc09). The reason why the last JA4 section is different even though the JA3 hash is the same is because some of these TLS handshakes present a different set of signature algorithms, which is a parameter that isn't being used in JA3.
Alerts Tab
CapLoader’s Alerts tab now includes more alert types than before and each alert has a severity rating graded as follows:
- High = 4
- Medium = 3
- Low = 2
- Info = 1
A typical high-severity alert is when a known malicious protocol is detected, while an “Info” type alert can provide a heads up about traffic from things like coin mining or legitimate remote admin tools. As you can see in the screenshot below the alerts are sorted based on severity to make it easier to prioritize them.
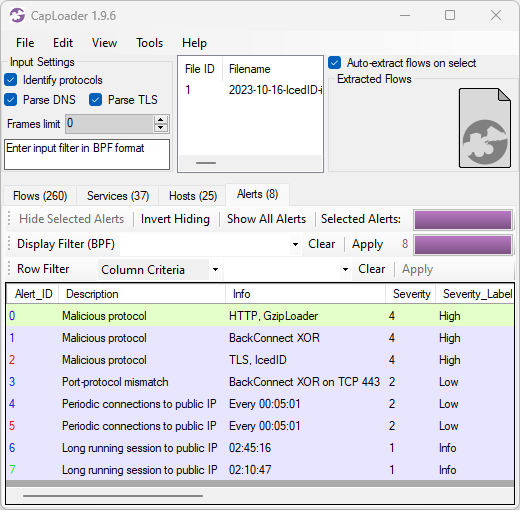
Image: CapLoader alerts for 2023-10-16-IcedID-infection.pcap
Here’s a breakdown of the alerts shown in the CapLoader screenshot above:
- GzipLoader traffic to 104.21.7.13:80 / aptekoagraliy[.]com
- BackConnect XOR traffic to 159.89.124.188:443
- IcedID over TLS traffic to 104.223.118.109:443 / seedkraproboy[.]com
- Port-protocol mismatch (non-TLS traffic to port 443) for 159.89.124.188:443
- Periodic connections every 5 minutes to 151.236.9.107:443 / lazirusairnaf[.]com
- Periodic connections every 5 minutes to 104.223.118.109:443 / seedkraproboy[.]com
- Long running TCP session to 159.89.124.188:443
- Long running TCP session to 104.248.81.48:443 / joekairbos[.]com
All these alerts are indicators of an IcedID infection, including the 5 minute C2 connection interval which I have mentioned before.
Other User Interface Improvements
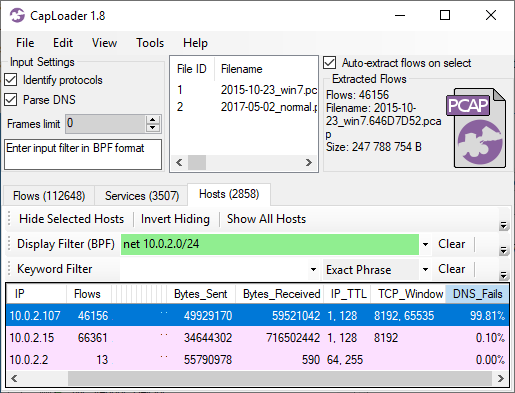
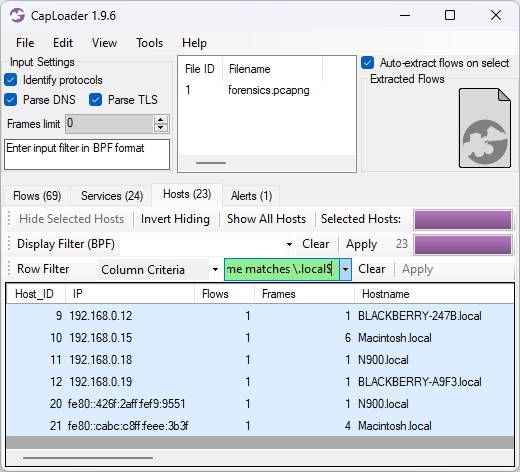
CapLoader’s “Column Criteria” row filter could previously only be used to filter on columns with a specific value, such as “Protocol = TLS”. This new release of CapLoader additionally allows users to do substring matching with the “contains” keyword and regular expression (regex) matching with the “matching” keyword. In the screenshot below the Column Criteria “Hostname matches \.local$” is used to only show hosts that have a hostname ending with “.local”.
We’ve also added an often asked for feature to CapLoader, namely the ability to switch between different flows in the Transcript window.
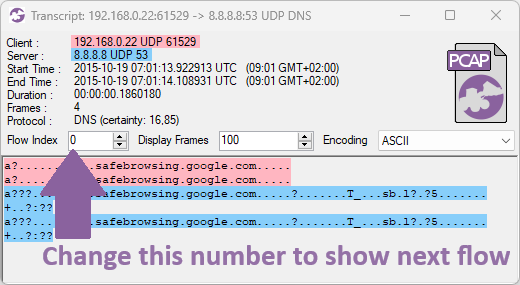
The flows you can switch between depends on how the transcript window was opened. A flow transcript opened from the Flows tab will allow switching between the flows that were visible in the list from where the transcript was opened. A transcript opened from any of the other tabs (Services, Hosts or Alerts), on the other hand, allows switching between the different flows for the particular service, host or alert that was opened.
Credits
I would like to thank Nic Cerny, Trent Healy and Fredrik Ginsberg for their input on various improvements that have been implemented in CapLoader 1.9.6.
Updating to the Latest Release
Users who have already purchased a license for CapLoader can download a free update to version 1.9.6 from our customer portal or by clicking “Check for Updates” in CapLoader’s Help menu.
Posted by Erik Hjelmvik on Wednesday, 15 November 2023 12:08:00 (UTC/GMT)
Tags: #CapLoader #ThreatFox #JA3 #JA4 #IcedID #GzipLoader #regex