Erik Hjelmvik
,
Saturday, 02 February 2013 22:10:00 (UTC/GMT)

On January 26 several users in China
reported
SSL
problems
while connecting to the software development site GitHub.com.
The reports indicated that the Great Firewall of China (GFW) was used to perform a Man-in-the-Middle (MITM) attack against users in China who were visiting GitHub.
This attack was most likely conducted in order to track which users that were reading or contributing to the
list of persons behind the GFW, which is hosted on GitHub.
There is a good
writetup on the attack by GreatFire.org, which says:
”At around 8pm, on January 26, reports appeared on Weibo and Twitter that users in China trying to access GitHub.com were getting
warning messages about invalid SSL certificates. The evidence, listed further down in this post, indicates that this was caused by a man-in-the-middle attack.
[...]
It was very crude, in that the fake certificate was signed by an unknown authority and bound to be detected quickly. The attack stopped after about an hour.”

Screenshot of SSL error at github.com by @bitinn
An important part of evidence, which was
used
in
the
coverage
of this incident, was a packet capture file named
github.pcapng
that was anonymously uploaded to CloudShark.
A self-signed X.509 certificate file, named github.com.crt, was also used as evidence.
It is, however, easy to extract X.509 certificates from PCAP files,
so the github.com.crt file might come from the github.pcapng capture file at CloudShark.
We have no reason not to trust the reports coming from users in China, who have been victims of this MITM attack.
However, in the spirit of “Trust, but verify” I decided to perform some network forensic analysis on the capture file.
More specifically I set out to answer the following questions:
| Q1 :
| Is the user a victim of a real attack rather than having staged and recorded a MITM attack set up by himself? |
| Q2 :
| Is the user located in China? |
| Q3 :
| What can we say about the technology being used for the MITM? |
Time-to-Live Analysis
My first step was to load the PcapNG file from CloudShark in CapLoader:
File > Open URL > Enter:
http://www.cloudshark.org/captures/cbdd11b20a5c/download
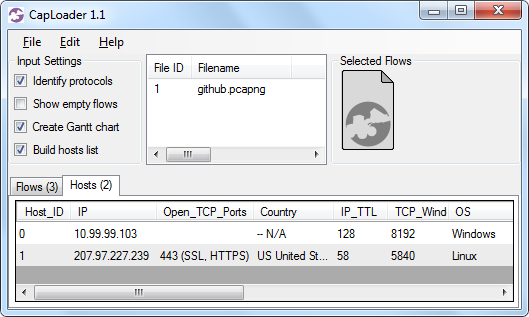
The “Hosts” tab shows that the capture file only contained traffic between two network hosts;
the user's machine and the GitHub server.
I also noticed that the GitHub server (207.97.227.239) had an IP TTL of 58 and TCP Window Size of 5840.
This values are a typical indication of the host being a Linux machine (see our
passive OS fingerprinting blog post for more details).
However, when connecting to GitHub.com from here (Sweden) the same server has an IP TTL of 128 and Window Size 64240.
This looks more like a Windows machine, and is significantly different from what the Chinese user got.
It can also be noted that a TTL of 58, which the Chinese user got, would mean that the SSL connection was terminated just six router hops away from the user.
However, a
traceroute from ihep.ac.cn
(in Beijing, China)
to github.com requires a whopping 16 hops.
Additionally, this traceroute hasn't even left Beijing after six hops.
traceroute to 207.97.227.239 (207.97.227.239), 30 hops max, 38 byte packets
1 gw (202.38.128.2) 0.231 ms 0.175 ms 0.178 ms
2 202.122.36.1 (202.122.36.1) 0.719 ms 0.626 ms 0.652 ms
3 192.168.1.25 (192.168.1.25) 0.509 ms 0.485 ms 0.459 ms
4 8.131 (159.226.253.77) 0.516 ms 0.488 ms 0.496 ms
5 8.198 (159.226.253.54) 11.981 ms 0.913 ms 0.829 ms
6 8.192 (159.226.254.254) 40.477 ms 40.614 ms 40.524 ms
7 Gi6-0.gw2.hkg3.asianetcom.net (203.192.137.173) 53.062 ms 40.610 ms 40.617 ms
8 te0-3-0-0.wr1.hkg0.asianetcom.net (61.14.157.249) 42.459 ms 43.133 ms 43.765 ms
9 te0-1-0-0.wr1.osa0.asianetcom.net (61.14.157.58) 76.603 ms 76.586 ms 76.648 ms
10 gi6-0-0.gw1.sjc1.asianetcom.net (61.14.157.98) 195.939 ms 195.934 ms 196.090 ms
11 ip-202-147-50-250.asianetcom.net (202.147.50.250) 180.966 ms 181.058 ms 181.339 ms
12 dcx2-edge-01.inet.qwest.net (67.14.28.70) 342.431 ms 340.882 ms 338.639 ms
13 67.133.246.158 (67.133.246.158) 253.975 ms 253.407 ms 253.742 ms
14 vlan905.core5.iad2.rackspace.net (72.4.122.10) 253.468 ms 252.947 ms 253.639 ms
15 aggr301a-1-core5.iad2.rackspace.net (72.4.122.121) 253.767 ms 253.862 ms 253.010 ms
16 github.com (207.97.227.239) 254.104 ms 253.789 ms 253.638 ms
MAC Address
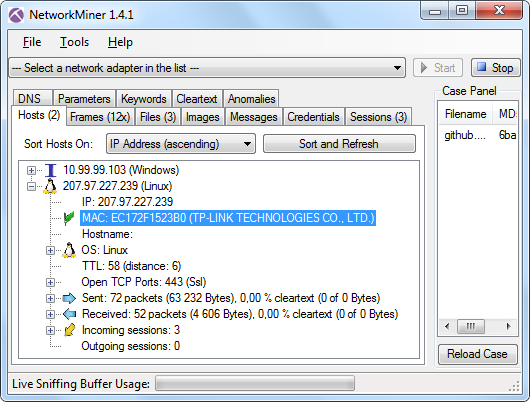
As shown in the NetworkMiner screenshot above, the Ethernet MAC address of the client's default gateway is ec:17:2f:15:23:b0,
which indicates that the user's router was a device from TP-LINK.
TP-LINK is a large provider of networking devices who make more than half of their sales within China.
This supports the theory that the user was located in China.
PcapNG Metadata
As we've mentioned in a previous blog post, PcapNG files can contain a great deal of metadata.
I therefore wrote a simple parser to extract all the juicy metadata that was available in the github.pcapng file that was anonymously uploaded to CloudShark.
The metadata revealed that the user was running “64-bit Windows 7 Service Pack 1, build 7601” and sniffing with “Dumpcap 1.8.2 (SVN Rev 44520 from /trunk-1.8)”,
which normally means that Wireshark 1.8.2 was being used (since it uses dumpcap for all packet capturing tasks).
The PcapNG file additionally contained a great deal of Name Resolution Blocks,
i.e. cached DNS entries.
Among these entries was an entry that mapped the IP 10.99.99.102 to the hostname “SHAOJU-IPAD.local”.
So why was there a name resolution entry for an IP address that wasn't part of the capture file?
Well, cached name resolution entries aren't properly cleaned from PcapNG files written with Wireshark 1.8.0 to 1.8.3 due to a
vulnerability discovered by
Laura Chappell.
So, who is “Shaoju”?
Well, a Google query for shaoju github will bring you to the GitHub user
Chen Shaoju, who also
tweeted a screenshot of the SSL error he received when accessing GitHub.com.
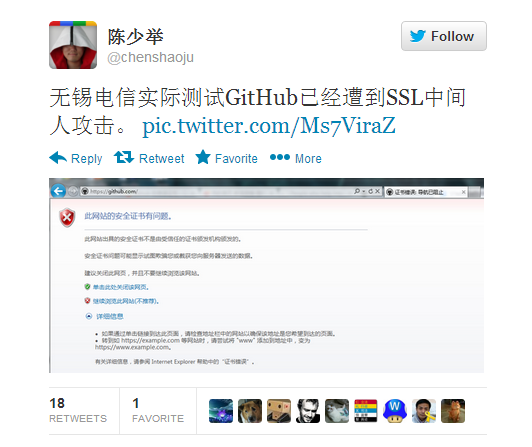
Conclusions
|
Q1 :
|
Is the user a victim of a real attack rather than having staged and recorded a MITM attack set up by himself? |
|
A1 :
|
Yes, this is most likely a REAL attack.
I'd find it unlikely that a user trying to fake such a MITM attack would use an environment with six router hops between the client and MITM machine.
|
|
Q2 :
|
Is the user located in China? |
|
A2 :
|
Yes, I'm convinced that the PcapNG file was sniffed by
Chen Shaoju, who lives in
Wuxi, China
according to his GitHub profile.
|
|
Q3 :
|
What can we say about the technology being used for the MITM? |
|
A3 :
|
The fact that the MITM machine was six hops away from the user indicates that the MITM is taking place at some fairly central position
in China's internet infrastructure, as opposed to being done locally at the ISP.
Additionally, the machine doing the MITM seems to be running Linux and having an initial IP TTL of 64 and a TCP Window Size of 5840.
|
UPDATE (February 5) : Privacy / Anonymity
The fact that this blog post reveals the identity of the anonymous
github.pcapng uploader seems to have caused
some
reactions online.
I did, however, contact Chen Shaoju before publishing this blog post.
In fact, I even sent him an email as soon as we discovered that it was possible to identify him through the capture file's metadata.
Here's what I wrote:
“I'm working on a blog post about the GitHub pcap file on CloudShark.
My analysis indicates that you sniffed the traffic. Is it OK with you
if I publish this blog post?
If not, then I'd recommend that you remove the pcap file from
couldshark in order to prevent others from identifying you via your
pcap file.”
Shaoju responded the same day and said it was OK.
Once the text for the blog post was finished I also sent him a copy for verification before we published it online.
Again, Shaoju responded swiftly and said that it looked good.
Also, I'm sure that Shaoju
(@chenshaoju) can confirm that this blog post was published with his consent.
Finally, I'd like to add a few recommendations to users who wish to preserve their anonymity when sharing capture files:
-
Filter out any traffic that isn't relevant to what you wish to share.
CapLoader is a handy tool for selecting and filtering capture files based on flows or IP addresses.
-
Save the capture file in the old libpcap (PCAP) format.
This will remove the metadata available in Pcap-NG option fields.
-
Anonymize frame headers, i.e Ethernet MAC addresses or even IP addresses (if needed), with a tool like:
tcprewrite,
Bit-Twist or
TraceWrangler.
Posted by Erik Hjelmvik on Saturday, 02 February 2013 22:10:00 (UTC/GMT)
Tags: #GitHub
#PcapNG
#China
#GFW
#Forensics
#MITM
#SSL