Erik Hjelmvik
,
Tuesday, 15 June 2021 11:55:00 (UTC/GMT)

We are happy to announce the release of NetworkMiner 2.7 today!
The new version extracts documents from print traffic and pulls out even more files and parameters
from HTTP as well as SMB2 traffic.
We have also updated our JA3 implementation to fingerprint the server side in TLS sessions using JA3S hashes
and added a few tweaks to the user interface to better identify the extension of extracted files.
Extraction of Printed Data
NetworkMiner 2.7 can extract documents from LPR/LPD print traffic on TCP 515
(RFC1179).
The extracted print data is saved to disk as .prn files, which can be analyzed with tools like
PCL Paraphernalia.
The professional version of NetworkMiner
also comes with a carver that attempts to extract PostScript and PDF files from print traffic.
Improved File Extraction from PCAP
One of the premier features of NetworkMiner is its ability to extract transferred files from network traffic.
We have fine tuned NetworkMiner’s file extraction code for SMB2 as well as HTTP POST in this release,
in order to retrieve as much information as possible from these protocols.
We’ve also added more granular logging of SMB2 requests and responses to the Parameters tab.
More DNS Types Supported
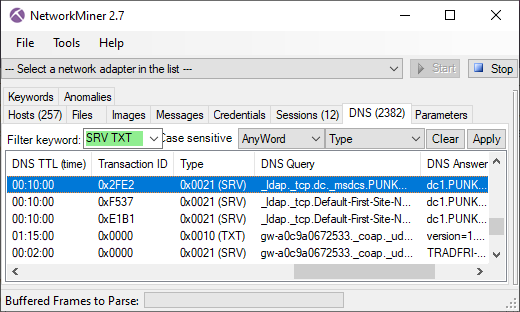
NetworkMiner 2.7 now parses DNS TXT and SRV resource records, which are displayed in NetworkMiner’s DNS tab.
The TXT records can be used for almost anything, but the SRV records are used to map service types to the hostnames that provide that service.
SRV lookups are often used in order to locate the domain controller on a network by querying for
“_ldap._tcp.dc._msdcs.<DOMAIN>”.
DNS SRV of lookups are performed by malware and attackers as well as for legitimate reasons, even though attackers
sometimes make mistakes that can be used for detection or threat hunting.
TLS Server Fingerprinting with JA3S
We introduced TLS client fingerprinting using
JA3 hashes in NetworkMiner 2.5.
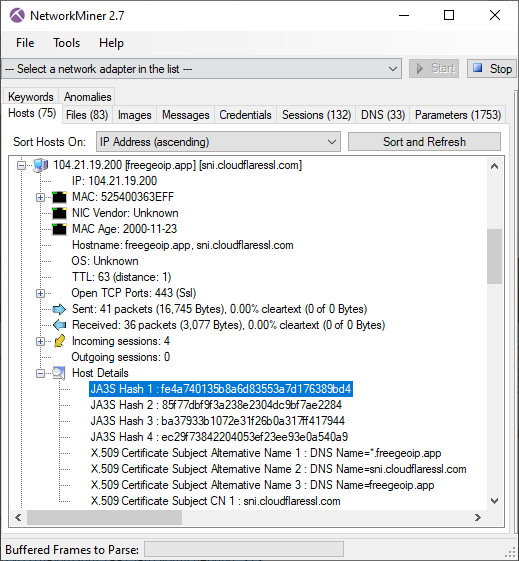
We have now also added support for JA3S hashes, which is a method for fingerprinting the server side of a TLS connection.
The JA3S hashes are extracted from the “Server Hello” TLS packets and shown on NetworkMiner’s Parameters tab as well as in the Host Details of the server.
We have also improved how NetworkMiner displays the JA3 hashes in the Host Details view.
Additional User Interface Improvements
Double clicking on an extracted file in NetworkMiner's Files tab now brings up the File Details window.
We’ve extended this window to also include a simple hex viewer and a feature that attempts to identify the file type based on the reassembled file’s header.
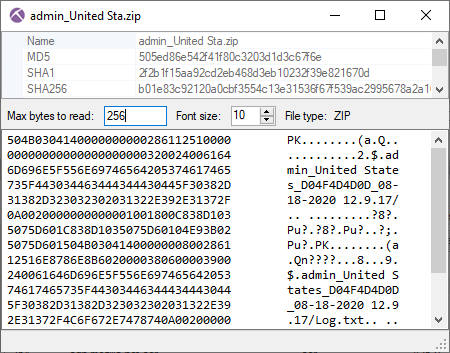
The file type identification feature is also used in order to provide more accurate file extensions to extracted files,
such as “.exe” or “.zip”, instead of the “.octet-stream” that you’d often see in previous versions of NetworkMiner.
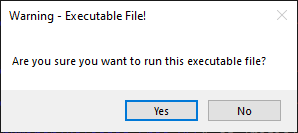
We have added a warning dialogue to NetworkMiner 2.7 that shows up if a user tries to run an executable file directly from the NetworkMiner GUI.
NetworkMiner Professional
Our commercial tool NetworkMiner Professional has received a few additional updates.
It can, for example, carve PDF and PostScript files from extracted LPR print data.
We have also added several OSINT services, such as ANY.RUN, MalwareBazaar, URLHaus and ThreatFox, for performing lookups of file hashes.
The OSINT context menu is opened by right-clicking an extracted file in NetworkMiner Professional.
GPS data stored in pcap-ng option fields, typically by Kismet, is now extracted as capture file metadata.
Right-click a capture file and select "Show Metadata" to show the coordinates from Kismet.
We have also re-implemented the support for a PCAP-over-IP listener in NetworkMinerCLI, which is the command line version of NetworkMiner Pro.
This feature allows the command line tool to receive PCAP data over a TCP socket instead of reading from a capture file.
The PCAP-over-IP listener feature was previously broken in NetworkMinerCLI.
Credits
We’d like to thank Hayo Brouwer (of Ricoh) for requesting the LPR extraction feature and providing capture files for testing,
Jeff Rivett for reporting a 64 bit issue with WinPcap/Npcap and Ali Mohd for reporting the broken PCAP-over-IP listener feature.
Upgrading to Version 2.7
Users who have purchased NetworkMiner Professional can download a free update to version 2.7 from our customer portal,
or use the “Help > Check for Updates” feature.
Those who instead prefer to use the free and open source version can grab the latest version of NetworkMiner from the official NetworkMiner page.
Posted by Erik Hjelmvik on Tuesday, 15 June 2021 11:55:00 (UTC/GMT)
Tags:
#NetworkMiner
#LPD
#LPR
#PCAP
#SMB2
#JA3
#JA3S
#ANY.RUN
#ThreatFox
#OSINT










